In this blog, we will discuss a technique to unpack most malware using Ollydbg. To start let us first look on the following useful Ollydbg features. We will be using these features for unpacking a malware sample.
- F9 - Run the program
- F2 - Set breakpoint
- ALT+F9 - Return to user code
- CTRL+G - Go to an expression, e.g., specific address, address of API or addresses pointed by the registers.
- Follow in Dump - This allows to view the contents of a memory in Ollydbg's memory address view.
We will be using a real malware that came from a spam. You can find the virustotal hits of this sample here. You also notice that it is not using a commercial packer.
Let us now unpack the sample.
1. Load the sample in Ollydbg.
2. Set breakpoint in VirtualAlloc. This is on the assumption that the sample uses VirtualAlloc api. In some cases it uses the native api, ZwAllocateVirtualMemory. To do this, press CTRL+G and type VirtualAlloc (case sensitive) then Enter. This will point you to the address of VirtualAlloc. Press F2 to set breakpoint.
3. Press F9 to run the sample.
4. If the breakpoint is hit, press ALT+F9 to go to back to user code.
5. Right click on the value of EAX on the registers section and click "Follow in Dump"
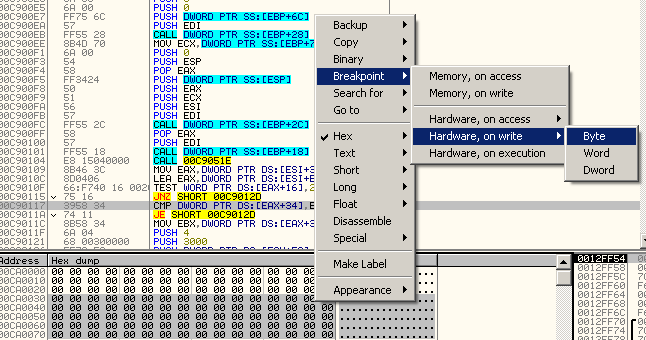
6. Highlight a few bytes on the Memory View and right click. Then select Breakpoint>Hardware, write>Byte. Then Press F9 to run again the sample. We do this because, when a sample uses VirtualAlloc, that means it is preparing to write something on the allocated memory. We wanted to breakpoint on that as soon as it is being written.
7. If the breakpoint is hit, examine the data. Is it already a PE image? In our case, not yet. Maybe it is still the second layer encryption routine. For this case, press F9 again to run the sample and hope that the VirtualAlloc is hit again.
8. Redo the steps 4,5 and 6.
9. Now the breakpoint is hit and we now see the MZ header. However, it seems it is not yet fully decrypted. We examine the code and it appears to be in a loop. This appears to be the last layer of decryption. Just finish the loop.
10. We are now looking at the decrypted PE file.
11. We just have to dump the memory and we have now an unpacked file.
Additional Notes:
In some cases, the sample is not using VirtualAlloc api so you might be wondering why your breakpoint is not hit. Try ZwAllocateVirtual memory or HeapAlloc. Also, the Breakpoint>Memory, on access can be used in placed for the hardware breakpoint.
Hope you learn something today. Cheers:)






dear Paul,
ReplyDeleteCan you do a similar tutorial to extract/dump newest dridex with OllyDbg 2? I find it's difficult to do it with version 2.
Hi yeurung,
DeleteCan you send me the hash of the sample?
Thanks
This comment has been removed by the author.
ReplyDeleteNice information. Thank you for sharing the information.
ReplyDeleteMoviebox apk
Moviebox download